
Fraudsters have always adapted to customer behavior, and today they’re exploiting one of the most trusted habits in banking: answering a phone call from “the bank.” Across the industry, criminals are posing as fraud department representatives, tricking customers into handing over credentials and one-time passcodes (OTPs).
These cases are not isolated incidents. They’re part of a recent wave of impersonation fraud targeting many banks we have spoken with lately. The wave is widespread, persistent, and effective because they prey on trust and urgency. Understanding the mechanics of the fraud MO (modus operandi) is the first step toward protecting both banks and customers.
How the Fraud Attack Works – Step by Step
- Initial Outreach. Fraudsters reach out by phone, posing as legitimate bank employees. Caller IDs are often spoofed, so the phone number looks like it really came from the bank.
- Building Credibility. To appear convincing, the attacker uses personal details already gathered from data breaches, or stolen data on the dark web, such as the client’s name, account type, or even recent transactions.
- The Request. Once trust is established, the criminal asks for a one-time passcode (OTP) “to verify identity” or “to secure the account.” In reality, they are attempting to log in to the client’s online banking session at that very moment. By handing over the OTP, the client unknowingly authorizes the attacker’s access.
- The Fake Website Trap. In some cases, victims are directed to a phishing site that looks identical to the bank’s login page. Entering credentials here sends them straight to the fraudster, along with the OTP the real bank generates.
The payoff is quick: attackers gain full access to accounts, can initiate transfers, change security settings, and lock out the rightful owner. All of this unfolds in minutes.
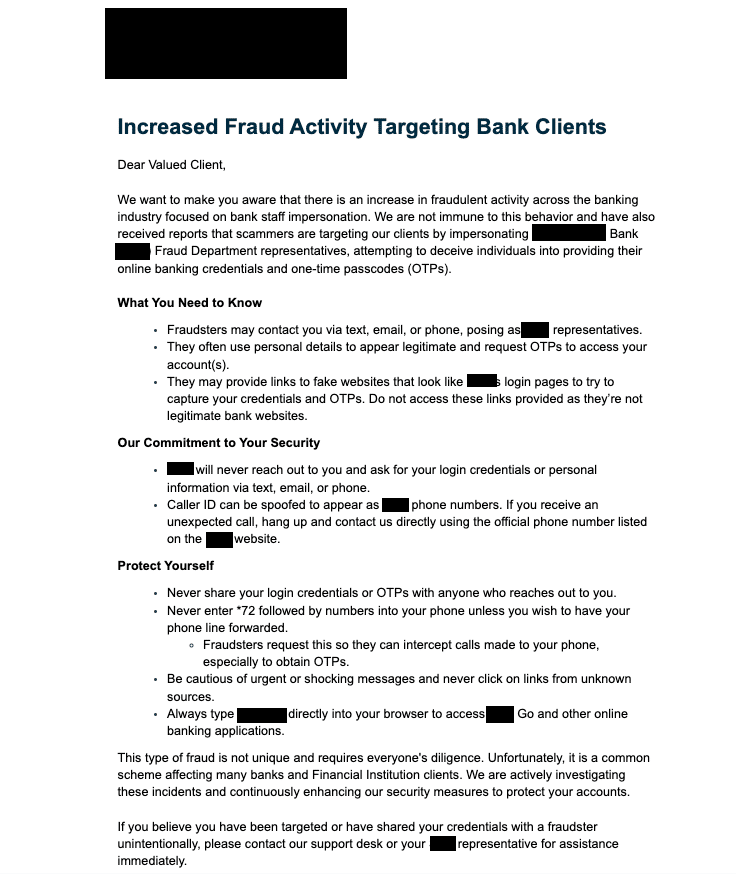
An urgent notice sent by a well-known U.S. bank to customers two weeks ago, warning them against this new wave of impersonation attacks.
Phone-Based Outreach Is at the Center of the Problem
These attacks succeed because customers have been conditioned to believe that a phone call from their bank is both urgent and trustworthy. Unfortunately, today’s technology undermines that trust.
- Caller ID spoofing is trivial. Fraudsters can make any number appear on a customer’s screen. Seeing the bank’s official number is no longer proof of authenticity.
- Voice is easy to manipulate. On the phone, tone and urgency can override rational caution. Customers may act in ways they wouldn’t if given time to reflect.
By continuing to rely on the phone as a primary communication channel, banks unintentionally reinforce the exact behavior fraudsters exploit: picking up and complying with a “bank representative.”
A Safer Path Forward
The solution isn’t less communication, quite the contrary: it’s smarter, verified and safer communications. Digital-first channels provide built-in safeguards that phone calls cannot.
This is where Refine’s Customer Outreach Platform plays a critical role. Refine enables banks to connect with customers through secure, digital-first channels like SMS, RCS, email, and push notifications, while removing the vulnerabilities of phone-based outreach. With fraud prevention built into its design, the platform ensures communications are trusted, authenticated, and seamless for customers. The result: banks can keep clients informed and engaged while dramatically reducing the risk of impersonation fraud. Fraudsters will continue to evolve. But by rethinking outreach and prioritizing verified digital communication, banks can protect their customers, safeguard their reputations, and stay one step ahead.







